Building the essentials of a ransomware response plan
September 22, 2025 | 3 minute read
Key takeaways
- Ransomware incidents can happen at any time to businesses of any size.
- Prioritize creating (or updating) a ransomware response plan.
- Stay informed about cyberthreats relevant to your industry and make cybersecurity a pillar of your business plan. It is integral to your company’s security.
Ransomware represents a persistent threat for businesses in every industry. This type of cybercrime can have severe impacts on organizations in terms of financial and data loss, regulatory compliance issues and reputational damage.
Not all organizations that fall victim report these incidents to authorities, and scope and severity assessments may vary from one organization to another. This makes it difficult to capture the crime’s full impact. However, security experts and law enforcement agencies report more sophisticated ransomware actors1 using novel methods2 and inflicting more losses every year.3
Improved and better-integrated security controls can thwart many ransom attempts and sometimes expose bad actors’ movements before they accomplish their objectives. However, no security apparatus is perfect, and cybercriminals continue to devise new ways to cripple digital infrastructure and coerce targets into meeting their demands.
A ransomware incident response plan is essential
Every organization needs a ransomware response plan that reflects its unique business needs, digital infrastructure, employee requirements and regulatory oversight. Moreover, incident response doesn’t end with the incident. In many cases, malicious actors can persist in the organization’s systems or exploit more than one entry point. A comprehensive response should include a forensic sweep to ensure the bad actors and malicious code are no longer in the business network and that no exploitable vulnerabilities remain unchecked.
The following guidelines can help you create an incident response framework that can adapt to your specific organizational or industrial requirements.
Key elements of a ransomware response plan
Ransomware response depends on a timely assessment of severity and reach, clearly defined roles and reactions, and a thorough investigation ensuring the threat is neutralized. An effective response plan depends on having a strategy in place before an incident occurs. Here’s how to get started.
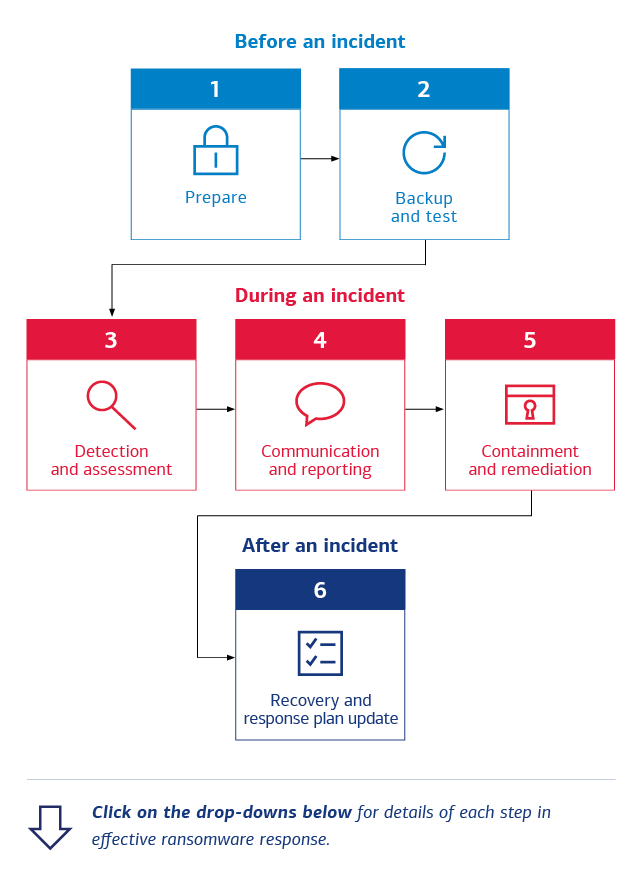
Before an incident:
1. Prepare
- Educate key personnel regarding current cyber-risks and objectives of cybercriminals.
- Create and maintain encrypted, offline or immutable backups of essential company data.
- Implement strong protections around identity and access management.
- Formulate, test and update a plan that identifies stakeholders and their roles, communication tactics and off-network channels, reporting procedures required by regulatory bodies or local law enforcement, and supports restoration of safe states.
2. Back up and test
- Regularly test and confirm the integrity of backups.
- Do not look at backups as the “last line of defense.” No backup method is 100% cybersecure, and stealthy bad actors can corrupt backups even before they launch ransomware.
During an incident:
3. Detection and assessment
- Use security tools to monitor network traffic for evidence of an adversary’s presence or movement and issue alerts.
- Assess which systems are compromised by ransomware and isolate them. Coordinate shutdown of all devices that cannot disconnect from affected systems.
- Reset all credentials and passwords connected to affected systems.
4. Communication and reporting
- Inform all internal teams and stakeholders on a preselected communication channel to ensure individuals essential to response are engaged.
- Report the incident as needed to affected third parties.
- Notify cybersecurity agencies and/or local law enforcement to maintain regulatory compliance or to receive additional assistance or guidance.
5. Containment and remediation
- Disable any system involved in the initial breach, as well as connected systems that malicious actors could use to access other parts of the company network or data systems.
- Analyze network traffic and endpoints for evidence of the malicious actors’ persistence. Remediate vulnerabilities.
- Rebuild the systems most critical to business operations.
- Reset passwords and permissions.
After an incident:
6. Recovery and response plan update
- Complete a thorough forensic analysis of the incident and document all steps taken to eliminate the ransomware or remove footholds the threat actor established.
- Confirm backups remain uncorrupted and don’t contain malicious payloads. Restore affected systems.
- Inform all relevant third parties and oversight agencies of the steps taken and removal of the threat.
- Make improvements to company systems based on forensics.
- Continue to maintain vigilance. Update security systems regularly and adapt employee training to reflect lessons learned.
1 Kaspersky, “State of Ransomware in 2024,” May 8, 2024.
2 Palo Alto Networks, “2023 Unit 42 Ransomware and Extortion Report”.
3 Internet Crime Complaint Center, “FBI Internet Crime Report,” 2022, 2023.
Explore more
Security & Information Management
Phishing. Vishing. Smishing. Keeping up with threats from scams, fraud and cyberattacks is difficult. Our resources and insights can help you protect your company and customers.
Important Disclosures and Information
Bank of America, Merrill, their affiliates and advisors do not provide legal, tax or accounting advice. Consult your own legal and/or tax advisors before making any financial decisions. Any informational materials provided are for your discussion or review purposes only. The content on the Center for Business Empowerment (including, without limitations, third party and any Bank of America content) is provided “as is” and carries no express or implied warranties, or promise or guaranty of success. Bank of America does not warrant or guarantee the accuracy, reliability, completeness, usefulness, non-infringement of intellectual property rights, or quality of any content, regardless of who originates that content, and disclaims the same to the extent allowable by law. All third party trademarks, service marks, trade names and logos referenced in this material are the property of their respective owners. Bank of America does not deliver and is not responsible for the products, services or performance of any third party.
Not all materials on the Center for Business Empowerment will be available in Spanish.
Certain links may direct you away from Bank of America to unaffiliated sites. Bank of America has not been involved in the preparation of the content supplied at unaffiliated sites and does not guarantee or assume any responsibility for their content. When you visit these sites, you are agreeing to all of their terms of use, including their privacy and security policies.
Credit cards, credit lines and loans are subject to credit approval and creditworthiness. Some restrictions may apply.
Merrill Lynch, Pierce, Fenner & Smith Incorporated (also referred to as “MLPF&S” or “Merrill”) makes available certain investment products sponsored, managed, distributed or provided by companies that are affiliates of Bank of America Corporation (“BofA Corp.”). MLPF&S is a registered broker-dealer, registered investment adviser, Member SIPC, and a wholly owned subsidiary of BofA Corp.
Banking products are provided by Bank of America, N.A., and affiliated banks, Members FDIC, and wholly owned subsidiaries of BofA Corp.
“Bank of America” and “BofA Securities” are the marketing names used by the Global Banking and Global Markets division of Bank of America Corporation. Lending, derivatives, other commercial banking activities, and trading in certain financial instruments are performed globally by banking affiliates of Bank of America Corporation, including Bank of America, N.A., Member FDIC. Trading in securities and financial instruments, and strategic advisory, and other investment banking activities, are performed globally by investment banking affiliates of Bank of America Corporation (“Investment Banking Affiliates”), including, in the United States, BofA Securities, Inc., which is a registered broker-dealer and Member of SIPC, and, in other jurisdictions, by locally registered entities. BofA Securities, Inc. is a registered futures commission merchant with the CFTC and a member of the NFA.
Investment products:

